Infrastructure & Network Security
Current NW Layout: High Availability NW Setup – EOSIO (TELOS/EOS) Block Producer
(Risks based Protection measures)
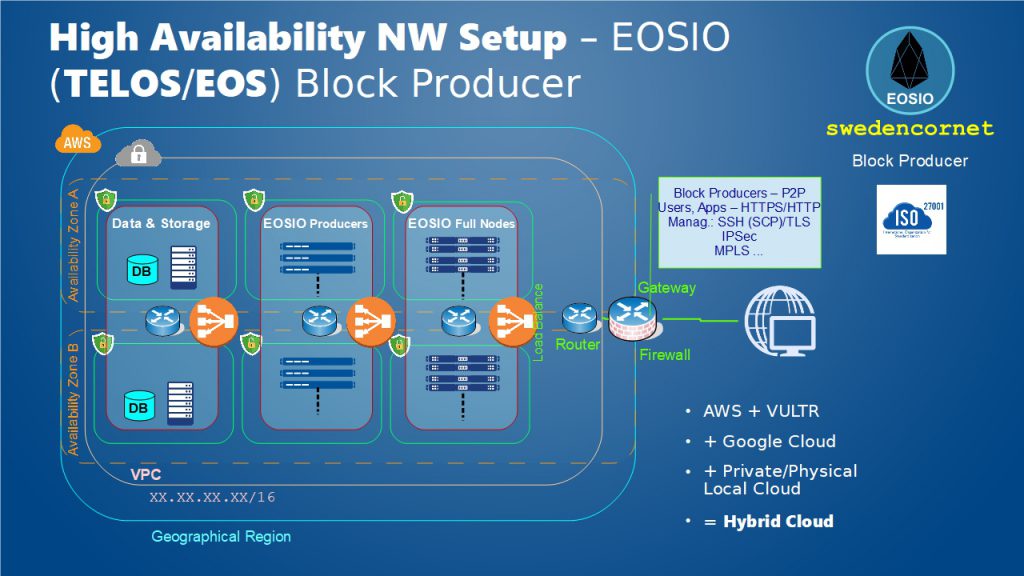
swedencornet has similar Network Layout for most EOSIO Chains e.g. Telos, MEETONE, Snax, EOS Mainnet, BOS, EOSForce, and so on.
We use highly secure, resilient, & reliable Bare Metal Severs at geographically safe and multiple locations for Blocks Production Nodes. For additional extra nodes we use reliable Cloud Service Providers that comply with CSA (Cloud Security Alliance) CCM (Cloud Controls Matrix) industry best practices. We also align our processes and procedures with Information Security best practices (ISO 27001/2, ISO 27005, ISO27017, ISO27018).
GRC (Governance, Risks, and Compliance Management) – EOSIO (TELOS/EOS)
swedencornet follows and take guidance from well-known universally accepted “Industry Best GRC Practices”.
- Telos Compliance:
Telos is a governed blockchain based on EOSIO. swedencornet is credited co-author and complies with all the main elements, requirements, and governance processes; including, but not limited to:- Telos Blockchain Network Operating Agreement (TBNOA).
- Telos Block Producer (BP) Infrastructure Requirements.
- Telos Block Producer (BP) Minimum Requirements.
- Telos Blockchain Network (TBN) Data Protection Policy.
- Telos ‘regproducer’ Human-language Contract.
- TBN Arbitration Rules and Procedures (TBNARP).
- TBN Arbitration Parameters Schedule.
- Telos ‘regarb’ Human-language Contract.
- Telos Arbitrator Minimum Requirements.
- Telos Compliance:
- EOS Mainnet Compliance:
swedencornet complies with the requirements, and governance processes as required by EOS Constitution; including, but not limited to:- EOS-Mainnet Governance Constitution.
We also support Block.one’s Proposal: Proposal for EOS Constitution v2.0.
Best practices & fundamentally sound principals in Information Security and Privacy
(Risks based Protection measures)
swedencornet is applying industry best practices and fundamentally sound principals in Information Security and Privacy to protect EOSIO (Telos/EOS) Block Production operations.
Everything at swedencornet is based on Risks Management principles. Meaning that selection and application of information security controls and measures are based on risk profiles. The cost of security controls and measures should not exceed the risk exposure. swedencornet is focusing on protection measures that should make it impractical for the bad actors to harm (or cause damage) to the swedencornet block production infrastructure, systems and services.
- Does 100% Security Exists?
Bitcoin Blockchain is considered most secure due to huge computing resources that are protecting the blocks. But is it 100% secure? The answer is BIG NO. Theoretically it is possible to execute 51% attack on Bitcoin Blockchain. But it is not particle for bad actors (most probably) to justify and execute such an attack due to the need of tremendous resources (both in terms of time and money). Moreover there is no guarantee that the bitcoin source code is 100% secure and it could behave unexpectedly (though it is extremely less likely). Neither it is guaranteed that all the bitcoin nodes and applications are configured properly in all environment to ensure protection in all unknown scenarios.
The point is that nothing in this universe is 100% secure, neither pure random numbers exist. And the whole point of security controls and measures is to make it impractical for the bad actors to succeed in compromising the target infrastructure, systems and services.
- Does 100% Security Exists?
- A BIG LIE and Piece of Advice:
If anyone (any EOSIO Block Producer or any other Person) is claiming that his/her infrastructure, systems and services are 100% secure…. then, I am sorry to say that “he/she is either lying or he/she knows nothing about information security”. Our piece of advice is to “NEVER give vote and trust to such an entity“….
- A BIG LIE and Piece of Advice:
Reference Network Layout for EOSIO Block Production based on Risk Profiles
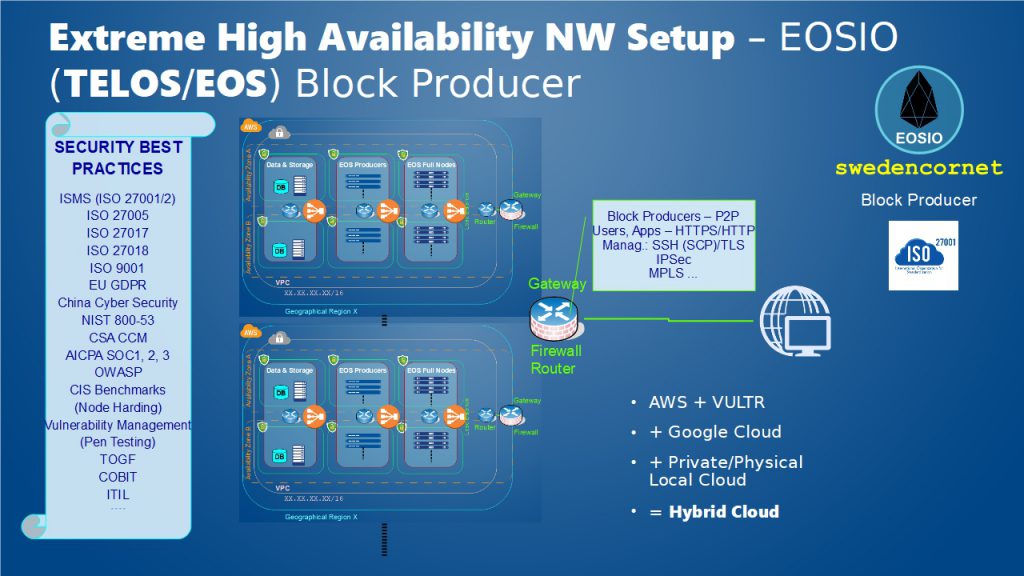
Based on Risks Management sound principles swedencornet is planning to follow the three NW Layouts (pictured and described below). Environment will change (it is not static), technology will change, understanding and knowledge will change; and hence the Risks will change. So the NW Layouts (pictured and described below) and needed security controls and measures will change. We are living in a dynamic and agile world.
Network Layout and Deployment based on your Risk Profile
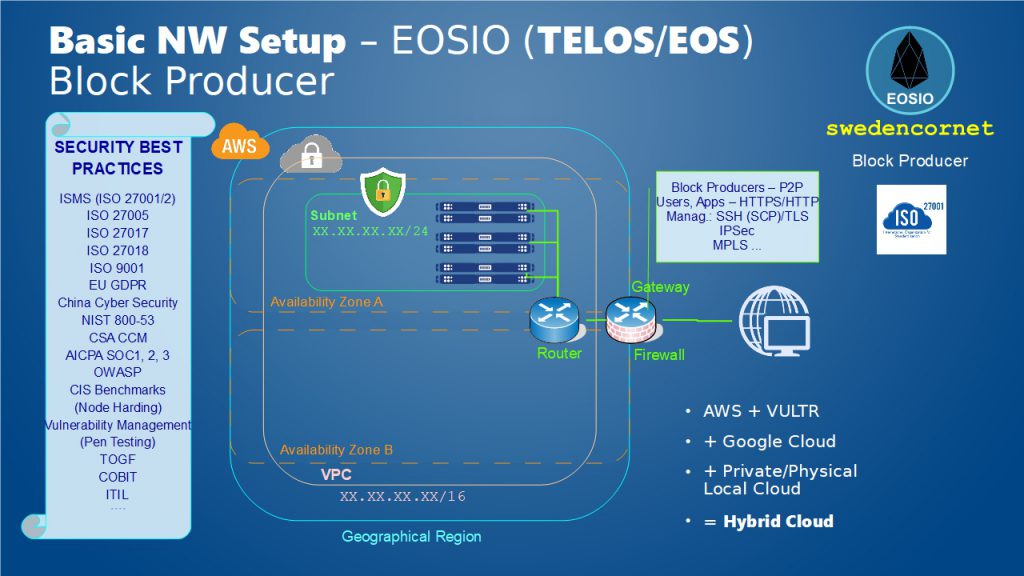
The best practice is to implement the network layout based on your risk profile and continuously adjust and improve it as threat profile changes. There is no one-fit solution for all Block Producers.
The 21 top Block Producers have different Risk Profile in comparison with other Block Producers (BPs) and they need tighten security controls and measures. The next range of standby Block Producers (BPs), let’s say from top 22 to 60, may have less risks and threats to coupe with while they are in standby. They may-not need same level of reliability and security as top 21 BPs. And then there is a whole different risk profile for the remaining standby Block Producer Candidates (BPCs). It does not make any justification and sense for a BPC, let’s say at nr 300, to implement and deploy network that supports same level of resiliency, fault tolerance, redundancy, and security measures that top-5 BPCs should have done it… But as the rank of BPCs goes up based on voting, the BPCs should be flexible enough to improve and enhance their capabilities in terms of scale-ability, reliability, agility and security.
The “BEST PRACTICE” is to implement and deploy the Network Layout based on your Risk Profile. So all there (3) layouts (pictured and described below) are best practices for the BPCs depending on which rank they have!
Note that one of the best practices, now-a-days, is that to use cloud services [whether it is Public Cloud, or Private on-premises Cloud (self owned and deployed Physical HW), or Hybrid]. Cloud brings lot of advantages in terms of scale-ability, reliability, agility and security. So at swedencornet we have taken the approach to go for cloud wherever practical (we may end up with Hybrid approach).
Basic NW Setup – EOSIO (TELOS/EOS) Block Producer
High Availability NW Setup – EOSIO (TELOS/EOS) Block Producer

Extreme High Availability NW Setup – EOSIO (TELOS/EOS) Block Producer
In-alignment with well-know, industry recognized Frameworks, Legislation and Standards
Note that, independent of which network layout, we are in today (and will be in future); swedencornet will always work in-alignment with these well-know, industry recognized frameworks, legislation and standards:

We are not sure if current top 21 EOS BPs follow any of the above basic MUST HAVE Frameworks, Legislations and Standards. We advice the voters to give special attention on this…